Airproxy Websocket Secure Transport
AirProxy is a transport feature that allows Airwall devices to connect using WebSockets over HTTPS (WSS). This enables Airwalls to operate in environments where standard control plane (MAP2 over TCP port 8096) and/or data plane (HIP over UDP port 10500) connectivity is blocked or restricted.
- Use Cases
-
Airproxy can be enabled in environments where any of theses conditions apply:
- TCP port 8096 is blocked
- UDP port 10500 is blocked
- 1500 byte packets cannot be delivered
- Use of a HTTP proxy is required
Prerequisites
- DNS must be configured for the relay hostname used in the TLS certificate, and the hostname must match the certificate’s Common Name (CN) to prevent connection failures.
- Firewall or security group rules must allow inbound TCP port 443 (HTTPS) to the relay.
- The Relay TLS certificate must be signed.
- Proxy configuration must support the HTTP CONNECT method, if an HTTP proxy is used.
- The Airwall must be running a supported version (For example, 3.3.0+ for Gateways, 3.3.4+ for Windows Agents).
Setup Airproxy
- In the Conductor, click on the Airwalls tab and select the Relay Gateway that you want to enable AirProxy for.
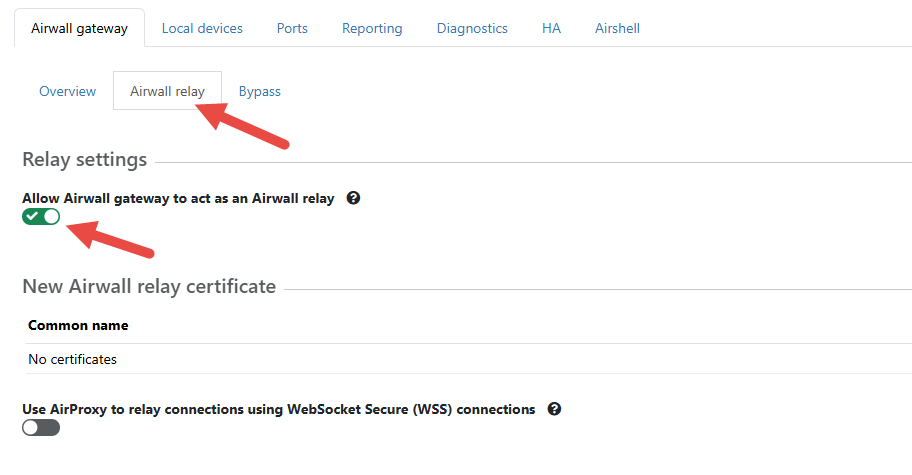
- On the Gateway page, click on Airwall Relay.
- From Relay settings, Enable Allow Airwall Gateway to act as an Airwall
Relay.
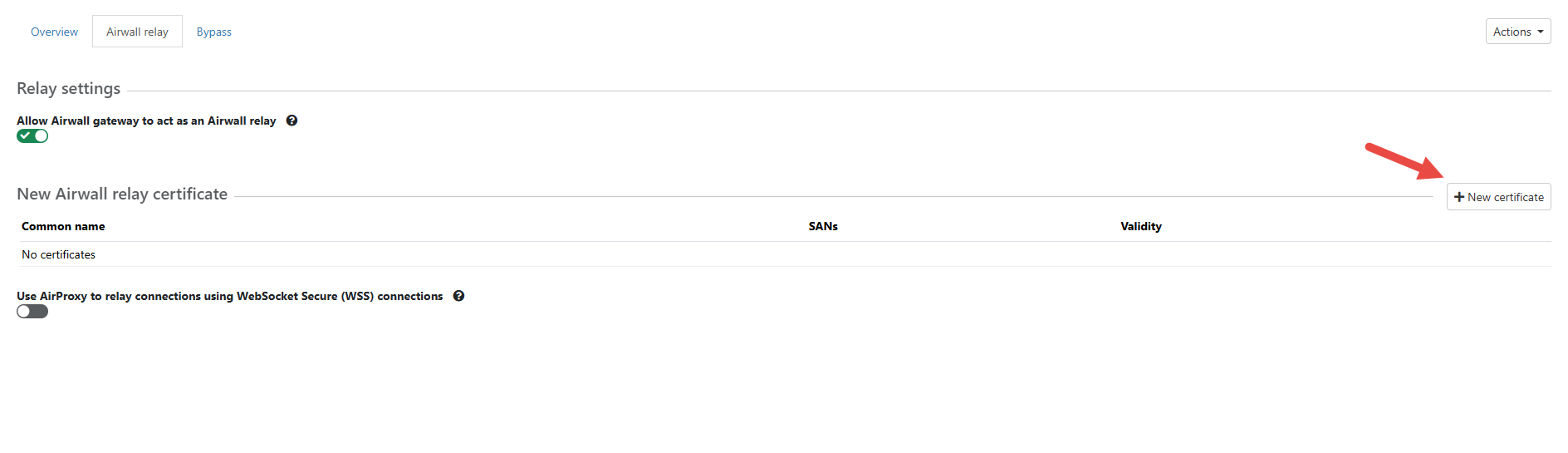
- From New Airwall Relay Certificate, click New Certificate. To
create a certificate, follow the page: Creating an AirProxy WebSocket relay certificate
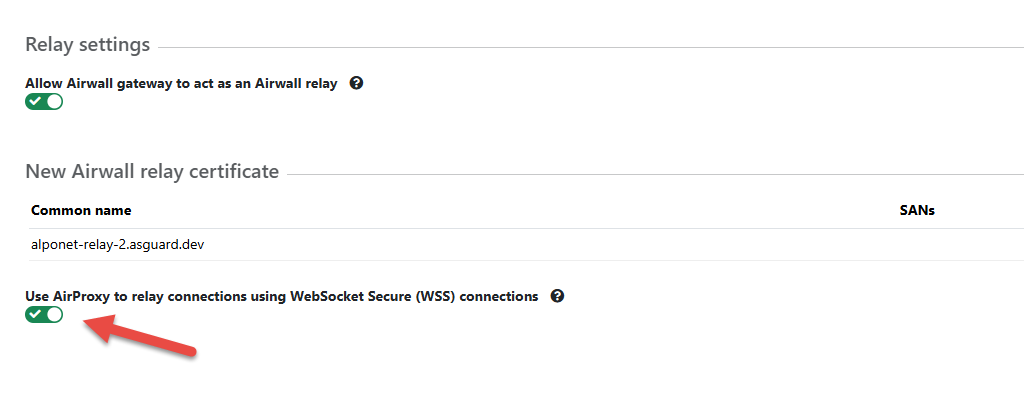
- Fill out the signed certificate details once ready.
- Enable Use AirProxy to relay connections using WebSocket Secure (WSS)
connections.
Connectivity Behavior
AirProxy handles both control plane and data plane traffic over WebSockets:
- MAP2 traffic tunnels over WSS to the Conductor.
- HIP traffic tunnels over WSS to the relay, which forwards it to the HIP daemon.
- Airwalls prefer UDP for HIP tunnels and fall back to WebSocket if UDP is unavailable.
- WebSocket fallback typically occurs ~90 seconds after startup or profile switch.
Troubleshooting
- Use airsh for diagnostics:
airsh» table wsmapproxy_sessions– View recent WSS MAP2 connections.airsh» table relay_probes– Check relay probe status.airsh» table hip_ws_sessions– Inspect HIP over WebSocket sessions.-
airsh» table websocket_proxy_connections– Active WSS connections on relay.
- In Conductor, look for the WSS icon in the Agent’s Status column.
Supported Versions
| Product | Version |
|---|---|
| Airwall Gateways | 3.3.0 and above |
| Airwall Embedded | 3.3.0 and above |
| Windows Agent | 3.3.4 and above |
| Linux Agent | 3.5.0 and above |
Best Practices
- Use AirProxy for low-bandwidth or edge deployments.
- Not recommended for high-volume or bulk data transfers due to TCP-in-TCP limitations.
- Always prefer UDP when available for HIP tunnels.
- Ensure all DNS and firewall prerequisites are met before enabling AirProxy.
Security Considerations
- AirProxy intentionally skips TLS certificate verification for relays to support enterprise environments where HTTPS traffic is intercepted by security appliances that replace certificates with internally signed ones.
- Authentication is enforced via MAP2 and HIP protocols.
- Avoid installing private CA certificates unless explicitly required.
Frequently Asked Questions
-
Q: Do I need to create special relay rules for AirProxy?
A: No special rules are needed beyond enabling AirProxy and ensuring DNS/firewall requirements.
-
Q: What if my organization uses an outbound HTTP proxy?
A: Configure the proxy via airsh. AirProxy supports HTTP proxies for egress.
-
Q: Does using WebSocket transport affect performance?
A: It can. WebSocket uses HTTPS over TCP, which is reliable but may slow down large data transfers due to how TCP handles congestion. For best performance, Airwall uses WebSockets only when UDP isn’t available.
-
Q: What if I want to configure an HTTP proxy for AirProxy connections?
A: If your network requires an HTTP proxy for outbound connections, you can configure it on the Airwall device that connects through the relay. This allows WebSocket Secure (WSS) traffic to traverse enterprise proxies that support the HTTP CONNECT method.
To configure the proxy:conf_proxy <proxy-url>Replace
<proxy-url>with your proxy server address (For examplehttp://proxy.example.com:3128).Note: This configuration is applied on the Airwall device using the relay, not on the relay itself where AirProxy is enabled.
For more details, refer to the page: Configuring a Conductor IP, Friendly URL, or Port
